When properly implemented, network authentication can serve as a powerful barrier against ransomware attacks, stopping bad actors before they gain the initial foothold they need.
In 2024, the number of attacks on US organizations actually went down by 7%, but that doesn’t mean that enterprise ransomware prevention is getting better. Unfortunately, the bad guys who deploy ransomware are learning to work smarter, not harder. More organizations are paying ransoms, and the average payments have spiked by 500% (as found by the Sophos State of Ransomware 2024 report).

Cybercriminals are working smarter, getting more money from fewer ransomware attacks
So who's getting targeted? The folks with valuable data, complex networks, and often inadequate protection. Universities, ISPs, and large enterprises find themselves squarely in the crosshairs.
While many organizations pour resources into firewalls and endpoint protection, they often neglect a critical first line of defense: their authentication systems. When properly implemented, strong network authentication can serve as a powerful barrier against ransomware attacks, stopping bad actors before they gain the initial foothold they need.
Why network authentication is your first line of defense
Most cybersecurity discussions start with perimeter defenses—firewalls, intrusion detection systems, and endpoint protection. But this approach overlooks a fundamental truth: the vast majority of ransomware attacks begin with compromised credentials. In fact, according to various threat reports, over 80% of breaches involve stolen or weak passwords.
Attackers don't need to breach your firewall if they can simply log in to applications with stolen credentials. Once they're in, they can move laterally through your network, escalate privileges, and deploy ransomware across critical systems. This is why authentication (the process of verifying who can access your network) and authorization (what they can do once inside)—must be your first consideration in ransomware prevention.
Without network authentication, your network and all applications are essentially open to local attackers. The firewall can block remote attacks, but it cannot do anything about an attacker sitting in the parking lot, using a shared WiFi WPA-PSK key.
When the network requires authentication, machines can be configured with client certificates independently of user accounts. The result is that an attacker cannot gain network access even if the user credentials are compromised. If they can’t gain network access, it is much more difficult for them to attack critical infrastructure.
At the risk of sounding reductive, you’ve got to close the barn door before the horse bolts. If you haven't prepared properly for the possibility of a ransomware attack, you will pay a steep price once it happens. Strong authentication is that barn door, and RADIUS is the gold standard for enterprise network authentication.
RADIUS: A strong foundation of enterprise network authentication and security
RADIUS (Remote Authentication Dial-In User Service) is the backbone of network authentication and authorization for approximately ¾ of enterprises worldwide—and for good reason. Though the "Dial-In" part of the name has become a nostalgic artifact (like the squeal of a modem), RADIUS has evolved into a comprehensive authentication framework that secures modern network access across wired, wireless, and VPN connections.
For universities managing tens of thousands of students and faculty, ISPs serving millions of subscribers, or enterprises protecting sensitive data, RADIUS provides the necessary infrastructure to verify users before granting network access. The protocol works by centralizing authentication decisions—when a user attempts to connect to your network, their credentials are verified against your user database before any access is granted. The authorization part of the RADIUS protocol provides a mechanism to define levels of access for users once they are authenticated.
What makes RADIUS particularly effective against ransomware is its ability to enforce granular access controls. Instead of providing a simple "yes" or "no" to network access, the authorization capabilities of RADIUS can specify exactly what resources users can access based on their identity, device, location, and other factors.
Even if user credentials are compromised, the attacker's ability to attack your internal network and deploy ransomware across critical systems can be severely limited if you have RADIUS authentication in place.
For ISPs, this means protecting infrastructure that serves thousands or millions of customers. For universities, it's about securing networks that handle everything from student records to groundbreaking research. For enterprises, it's safeguarding the very data that keeps the business running.
Just getting started with RADIUS? Learn more about RADIUS implementation.
Prevention Strategy #1: Robust authentication protocols
When implementing network authentication for maximum security, organizations face choices that may seem counterintuitive. Let’s break down authentication protocols in simpler terms:
Authentication protocols are the methods used to verify a user’s identity. Common protocols include:
- PAP (Password Authentication Protocol): Transmits passwords for verification
- CHAP (Challenge-Handshake Authentication Protocol): Uses a challenge-response mechanism
- MS-CHAP: Microsoft's version of CHAP
Surprisingly, PAP can be more secure than other methods, when it is implemented properly. Why? Because PAP allows passwords to be stored in the database in salted/hashed form (essentially encrypted), whereas CHAP and MS-CHAP require storing passwords as clear text in the database. If your database is ever compromised—a common first step in sophisticated ransomware attacks—hashed passwords are far more difficult for attackers to exploit than clear text ones.
To maximize authentication security against ransomware:
- Configure your authentication server to use PAP for authentication where possible.
- Ensure all authentication traffic is encrypted using TLS (Transport Layer Security).
- Implement strong password policies, including minimum length and complexity requirements.
- Use long, cryptographically random shared secrets (such as passwords, API keys, and encryption keys) between authentication clients and servers (not "testing123" or "password" - I've seen both used in production environments).
For universities with complex, distributed networks spanning multiple campuses, proper authentication and authorization configuration is crucial. By preventing unauthorized movement between network segments (such as between administrative systems and student networks), you can contain potential ransomware outbreaks even if an initial compromise occurs.
Prevention Strategy #2: Multi-factor authentication implementation
Multi-factor authentication (MFA) is perhaps the single most effective measure against credential-based attacks. When properly implemented with RADIUS, MFA can reduce the risk of successful account compromise by over 99%.
MFA works by requiring two or more verification methods before granting access:
- Something you know (password)
- Something you have (security token, mobile device)
- Something you are (fingerprint, facial recognition)
Technical implementation of MFA with RADIUS can take several forms:
- Token-based authentication using time-based one-time passwords (TOTP)
- Push notifications to mobile devices
- SMS-based verification codes (though this is increasingly vulnerable)
- Biometric verification where appropriate
ISPs face different challenges, needing to secure both customer access to user portals, and for employee administration of internal infrastructure. For customer-facing systems, streamlined MFA is essential. For internal administrative access to critical infrastructure, more robust verification methods should be employed, potentially including physical tokens or biometrics for privileged accounts.
In enterprise environments, role-based MFA that adjusts verification requirements based on the sensitivity of accessed resources can balance security with usability. Critical financial systems might require multiple verification factors, while routine access could use simplified verification.
New legislation in multiple jurisdictions requires that MFA is used for employee access to critical systems, especially ones which process financial data. RADIUS can help to centralize this MFA management, so that MFA does not need to be configured on each individual machine.
Prevention Strategy #3: Comprehensive backup strategy
Backups are your BFF. In ransomware prevention, a good backup strategy is non-negotiable. However, you need the right backups, properly secured and isolated from your main network.
Many organizations learn too late that their backups were either accessible to ransomware or weren't comprehensive enough to enable full recovery. Authentication systems can play a crucial role in protecting backup systems by:
- Restricting backup system access to specific administrative accounts
- Requiring elevated authentication for backup operations
- Logging all access attempts to backup systems for audit purposes
- Enforcing network segmentation that isolates backup infrastructure
For universities managing vast amounts of research data and student information, tiered backup strategies are essential. Critical data requires more frequent backups and stronger isolation. Consider implementing the 3-2-1 rule: three copies of your data, on two different media types, with one copy stored off-site.
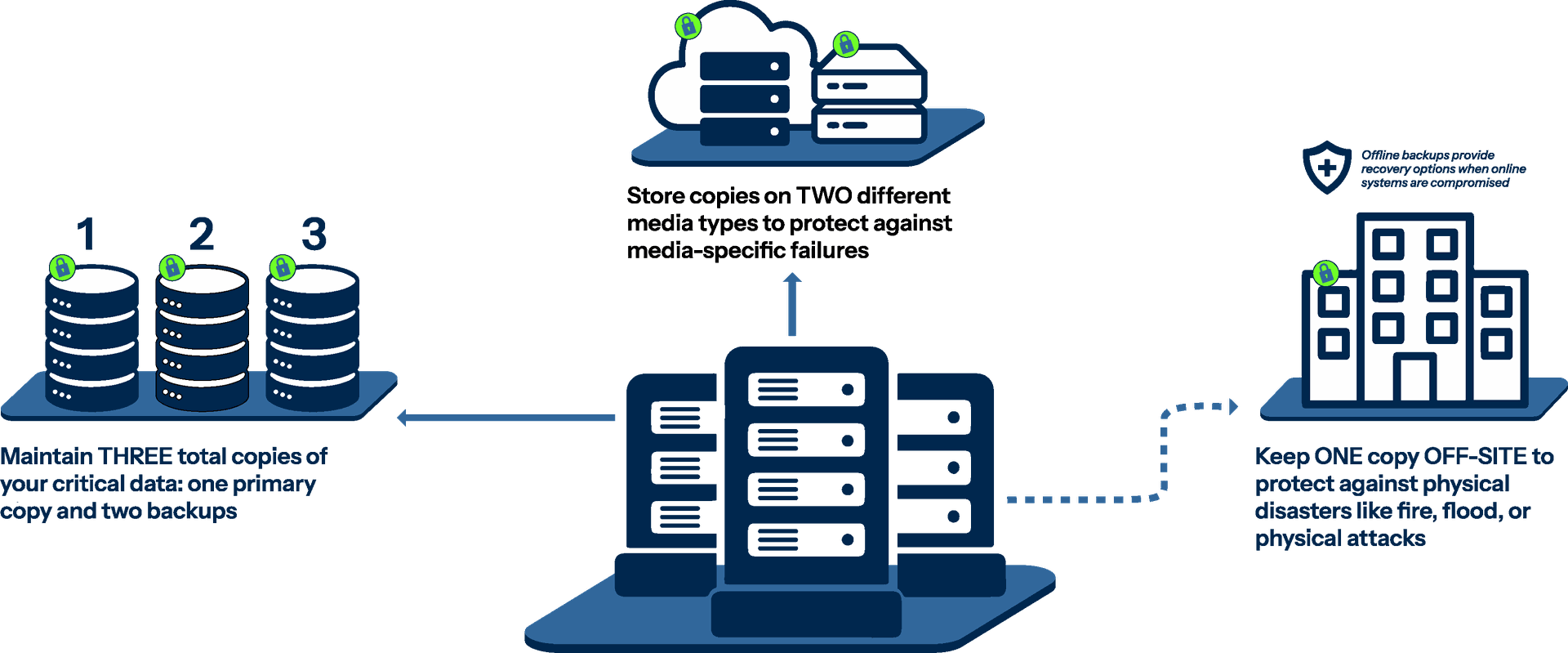
Ransomware resilience using the 3-2-1 rule
ISPs need to prioritize backing up configuration data and customer databases, which are essential for service restoration. These backups must be on a different network, completely segregated from production environments to prevent compromise.
Enterprise environments should implement backup verification processes that regularly test restoration capabilities, ensuring backups are not just present but actually functional when needed. I've seen too many organizations discover their backup systems weren't working only after they needed them.
In addition, off-site and off-line backups are a hard requirement. If your backups are co-located with your servers, then a disaster like a fire could destroy both. If your backups are online, then an attacker can simply log in to the relevant systems and delete them. Off-line and off-site backups ensure that backups are available to restore critical business data.
Prevention Strategy #4: Human-centric security approach
The human element remains both the greatest vulnerability and the strongest potential defense in cybersecurity. In general, the weakest link in your security framework is human beings. Most ransomware attacks happen when an employee innocently clicks on the wrong link in an email.
For universities with diverse user populations—from tech-savvy computer science students to less technical administrative staff and faculty—targeted training approaches are essential. Rather than generic network security awareness, focus on role-specific threats and behaviors.
Authentication logs can provide valuable insights for tailoring security training. By analyzing failed authentication attempts and unusual access patterns, security teams can identify departments or user groups that may need additional security awareness training.
For ISPs, training should emphasize the downstream impact of security failures—how a single compromised account could affect thousands of customers. For technical staff with high-privilege access, advanced team practice with real-world exercises is warranted.
In enterprise environments, regular simulated phishing campaigns can help maintain vigilance against the most common ransomware entry points. These should be followed by immediate training for those who fail the test, turning each potential vulnerability into a learning opportunity. Nobody wants to be the one who cost their employer millions of dollars, but they need cyber security training.
Prevention Strategy #5: Strategic IT investment
The most effective ransomware prevention strategies aren't blocked by technical limitations but by budgetary constraints. Despite understanding best practices, many organizations fail to implement proper protection simply because they don't allocate adequate resources to defending against cyber threats.
This misalignment between risk and investment is particularly pronounced in universities and educational institutions. As Lou Steinberg of CTM Insights notes, "Many universities are running very thin IT budgets ... Most universities underspend on technology because they're focused on their product, which is either education or research."
For network authentication security, this underfunding manifests in several critical ways:
- Outdated hardware running legacy systems: Many institutions operate authentication servers on aging hardware that lacks the processing power for modern encryption methods and MFA implementation.
- Insufficient staff for proper monitoring: Authentication logs contain early warning signs of compromise, but only if qualified personnel review them.
- Delayed security patches: Critical security updates for authentication systems often remain undeployed for months due to insufficient maintenance windows or staff time.
The reluctance to invest adequately in security infrastructure represents a profound misunderstanding of modern risk economics. When a 10TB external drive for secure backups costs less than $250, yet many IT departments struggle to get such minimal expenses approved, organizational priorities are dangerously misaligned with actual threats.
For universities protecting valuable research data, ISPs safeguarding customer information, and enterprises securing intellectual property, this approach is particularly shortsighted. The average ransomware payment now exceeds $2 million—thousands of times more than preventative measures would cost.
Like regular maintenance for vehicles prevents catastrophic breakdowns, consistent investment in authentication infrastructure prevents devastating security failures. We all invest in regular maintenance of our cars to prevent more costly repairs down the road. Network security also needs regular investment and maintenance.
Your insurance against disaster
Authentication and authorization-first security represents a fundamental shift in how organizations approach ransomware prevention. Rather than focusing exclusively on keeping attackers out, this approach acknowledges that perimeters will be tested and potentially breached. By implementing robust authentication and authorization through properly configured systems like RADIUS, organizations can significantly reduce the impact of such breaches.
For universities, ISPs, and enterprises, the message is clear: invest in authentication security now to prevent costly ransomware recovery later. Review your authentication implementation, upgrade authentication protocols, implement MFA, secure your backups, train your people, update your hardware and software, and allocate appropriate resources.
When it comes to ransomware, an ounce of prevention is worth far more than a pound of cure. It's worth a metric ton.
Need more help?
InkBridge Networks has been at the forefront of network security for over two decades, tackling complex challenges across various protocols and infrastructures. Our team of seasoned experts has encountered and solved nearly every conceivable network security issue. If you're looking for insights from the architects behind some of the internet's most foundational authentication systems, you can request a quote for network security solutions here.
Related Articles

Disaster-proof your network critical infrastructure
If you live in an earthquake zone, it’s important to engineer buildings to survive an earthquake. You don’t know when an earthquake will happen, or where exactly, or how big it’s going to be, but you know that it will happen at some point during the lifetime of the building. And the consequences of not earthquake-proofing can be deadly.

Preventing fraudulent logins with a session database
In today's enterprise computer networks, credential sharing is a big problem for ISPs and companies with multiple locations. When an ISP runs RADIUS servers across different sites, new attack vectors appear.