Global enterprises could lose millions of dollars in minutes without ironclad network security. Learn how industry leaders—including Goldman Sachs, Siemens, and a national US bank—protect critical data and infrastructure with the world’s most widely used authentication server, FreeRADIUS.
When Goldman Sachs needs to authenticate hundreds of thousands of connections daily, or when Siemens can't afford even an hour of network failure in their manufacturing plants, they don't compromise. They choose FreeRADIUS with InkBridge Networks' enterprise support.
In a world where a single security breach can cost a fortune and vendor lock-in can cripple your agility, the best solution isn't always the most expensive one. It's the one that gives you complete control, unlimited scalability, and 100% uptime—without the enterprise software price tag that makes your CFO's eye twitch. Here's how industry leaders discovered that the world's most trusted network access system is also its most practical.
The challenge: Securing global enterprise networks
Fortune 500 companies operate in environments where security and operations vulnerabilities can cost millions of dollars in minutes. These organizations face several critical challenges:
- Scale: Managing network authentication across thousands of switches and millions of ports worldwide
- Control: Ensuring only authorized users and devices can access corporate networks
- Resilience: Maintaining local network functionality even during internet outages
- Customization: Implementing security solutions that adapt to their unique infrastructure needs
- Governance: Centralizing security policy while distributing network infrastructure globally
Goldman Sachs needed to authenticate every wireless user and wired connection across their global operations. With critical financial transactions and sensitive client data at stake, even minor security vulnerabilities could expose them to significant risk.
Similarly, Siemens, with 320,000 employees across manufacturing facilities worldwide, required robust port-level authentication that wouldn't disrupt production if internet connectivity failed.
Factories like Siemens can't afford downtime due to authentication failures. Every minute of production stoppage costs thousands of dollars. Traditional cloud-based authentication solutions would introduce unacceptable risk. Local FreeRADIUS servers eliminate this dependency.
The solution: FreeRADIUS with enterprise support
After thorough evaluation of commercial and open-source options, these Fortune 500 companies selected FreeRADIUS, backed by InkBridge Networks' enterprise support.
Their decision was based on several key factors:
- Complete control: Unlike proprietary solutions, FreeRADIUS provided full visibility into the authentication system with full access to source code and functionality—a critical requirement for organizations handling sensitive data.
- Distributed architecture: The ability to distribute FreeRADIUS servers across facilities worldwide enabled local authentication even during WAN outages.
- Customization flexibility: The open-source foundation allowed for rapid implementation of customer-specific features without lengthy vendor development cycles.
- Enterprise-grade support: InkBridge Networks' deep expertise and same-business-day response times provided the assurance required for mission-critical systems.
- Cost-effective scaling: The solution allowed deployment of as many servers as needed without additional licensing costs, eliminating the "budget vs. security" dilemma.
Implementation: Securing every network connection
The enterprise implementations followed a similar pattern, with each organization deploying 20 to 200 FreeRADIUS servers across their global facilities.
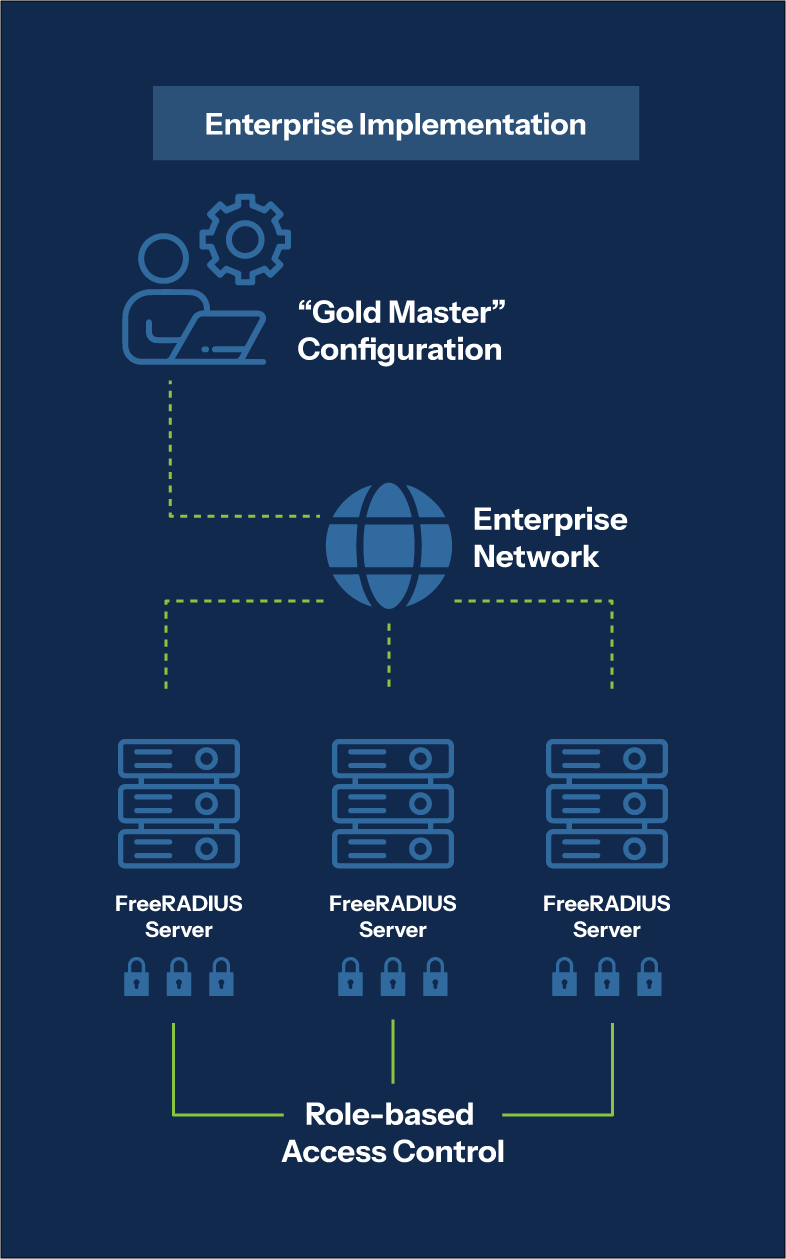
A typical deployment of local FreeRADIUS servers with centralized configuration
Key implementation elements included:
- Centralized management: All FreeRADIUS servers were configured and managed by central IT teams, following a "gold master" approach that ensured consistent security policies.
- Distributed authentication: Local FreeRADIUS servers provided authentication services for nearby network infrastructure, enabling continued operation during WAN outages.
- Defence-in-depth integration: FreeRADIUS became the first line of defence in a comprehensive security architecture, working alongside other security controls.
- Role-based administration: Local IT staff could manage and support end-user devices but lacked permissions to modify network authentication policies.
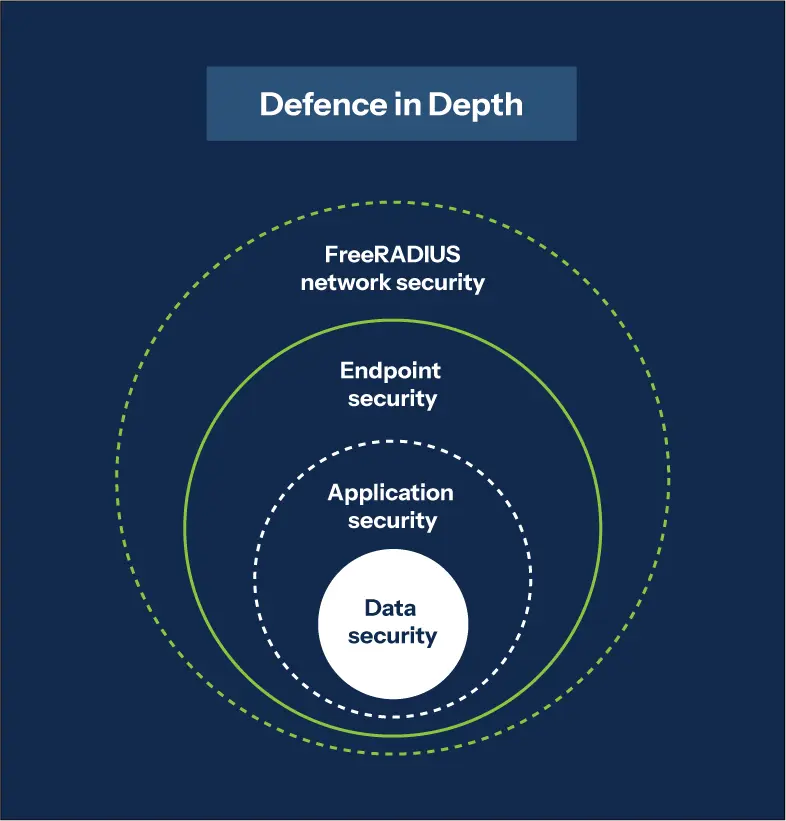
FreeRADIUS is the first of many layers of protection for enterprise infrastructure
One particularly illustrative example came from a manufacturing client:
"The central IT department initially proposed moving all authentication to their cloud services for simplified management. Our factory leadership immediately pushed back, noting that internet outages could cost us up to millions of dollars per hour in lost production. IT quickly revised their plan, deploying locally managed FreeRADIUS servers in our network closet that continued functioning regardless of WAN connectivity."
Results: 10+ years of secure, resilient operation
These Fortune 500 enterprises have now operated their FreeRADIUS implementations—in most cases, for over a decade—with remarkable outcomes:
- Zero FreeRADIUS-related security incidents across years of time, and millions of daily authentications
- 100% authentication uptime at local facilities, even during network disruptions
- Complete control over security policies and authentication requirements
- Fast turn-around time for support tickets. Responses and bug fixes take hours, not months.
- Significant cost savings compared to commercial alternatives
For Goldman Sachs, this translated to secure authentication for every wireless user and wired port worldwide. Siemens achieved comprehensive protection across their manufacturing operations without compromising production uptime.
The most telling result? These organizations contact InkBridge Networks for support only when they have questions, not when the system goes down. They value the relationship because the implementation works exactly as designed year after year. Support is being used for questions and answers about normal business requirements, and is not being used for emergency fire fighting. The result is low down times, increased confidence in the system, and a high degree of customer satisfaction.
Key takeaways for enterprise network security
The success of these implementations demonstrates several important principles for enterprise network security:
- Security without compromise: Properly implemented authentication can provide both security and operational resilience.
- Local resilience matters: Distributed authentication architecture prevents productivity losses during connectivity disruptions.
- Control is critical: Open-source solutions with proper enterprise support provide both transparency and assurance.
- Scale affordably: Organizations should deploy as many RADIUS servers as their security requires, not as many as their licensing budget permits.
- Expert support creates value: Even with minimal day-to-day needs, having direct access to the world's foremost FreeRADIUS experts provides confidence and rapid resolution when issues arise.
Get enterprise-grade support
InkBridge Networks provides enterprise network solutions focusing on Authentication, Authorization, and Accounting. The company created and maintains FreeRADIUS, the world's most widely deployed RADIUS server, supporting hundreds of millions of users daily.
With decades of experience in network authentication protocols, InkBridge Networks offers enterprise support, consulting, and custom development for organizations requiring robust security solutions that don't compromise on control or resilience.
Learn more about our enterprise solutions or contact us to discuss how we can help secure your network infrastructure.
Need more help?
InkBridge Networks has been at the forefront of network security for over two decades, tackling complex challenges across various protocols and infrastructures. Our team of seasoned experts has encountered and solved nearly every conceivable network security issue. If you're looking for insights from the architects behind some of the internet's most foundational authentication systems, you can request a quote for network security solutions here.
Related Articles

How authentication protocols work
There are a variety of authentication protocols to choose from, each with their own set of advantages, disadvantages, and constraints. In general, we recommend using PAP whenever possible. It is compatible with all known back-end databases, and it has no known security issues.

Authorized users only: Why use RADIUS and 802.1x to control network access?
Controlling which users and what devices are on your network has become significantly more complex in the current corporate environment. Network administrators must adapt to wireless access, remote working, bring-your-own-device scenarios and cloud computing.